Resecurity Released a 2024 Cyber Threat Landscape Forecast
Security Affairs
DECEMBER 26, 2023
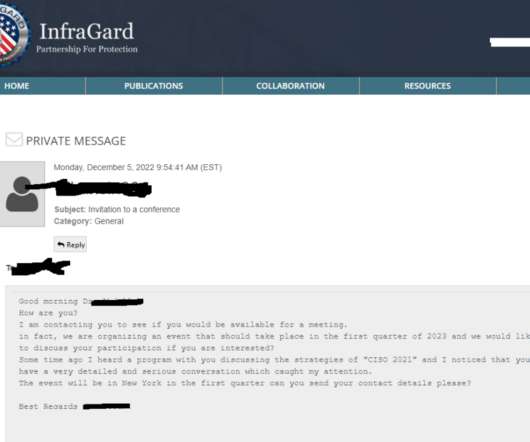
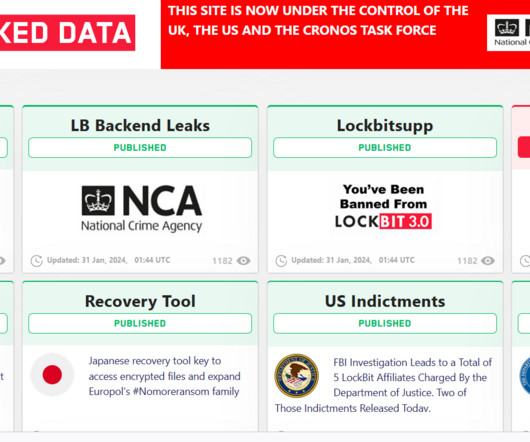
Securities and Exchange Commission regulations are expected to fuel heightened interest among malicious actors in orchestrating network intrusions and data breaches within these entities.




















Let's personalize your content