Russia-linked APT28 used new malware in a recent phishing campaign
Security Affairs
DECEMBER 29, 2023
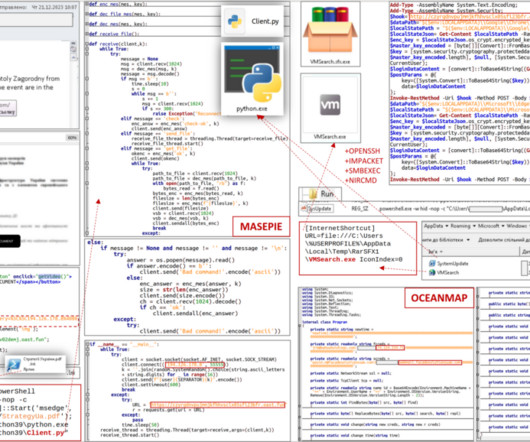
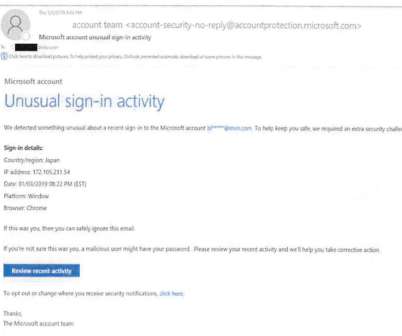
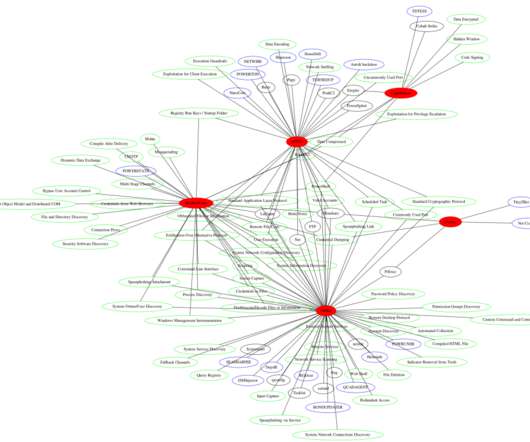
Ukraine’s CERT (CERT-UA) warned of a new phishing campaign by the APT28 group to deploy previously undocumented malware strains. The Computer Emergency Response Team of Ukraine (CERT-UA) warned of a new cyber espionage campaign carried out by the Russia-linked group APT28 (aka “ Forest Blizzard ”, “ Fancybear ” or “ Strontium ”).







































Let's personalize your content