Indictment, Lawsuits Revive Trump-Alfa Bank Story
Krebs on Security
SEPTEMBER 23, 2021
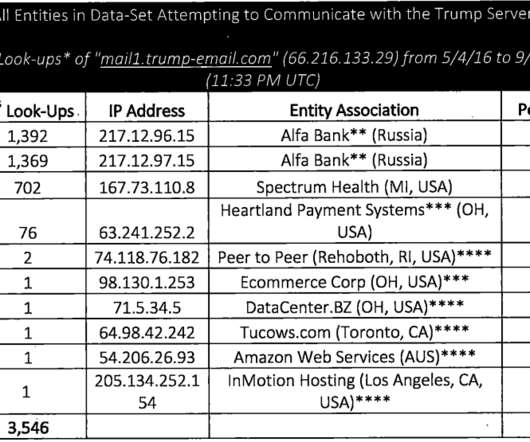
In October 2016, media outlets reported that data collected by some of the world’s most renowned cybersecurity experts had identified frequent and unexplained communications between an email server used by the Trump Organization and Alfa Bank , one of Russia’s largest financial institutions. trump-email.com).
















Let's personalize your content