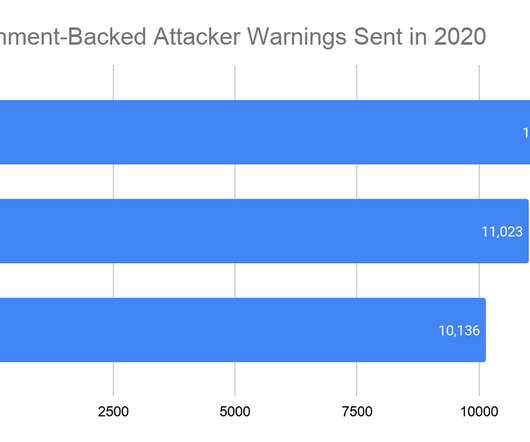
Google warned users of 33,015 nation-state attacks since January
Security Affairs
OCTOBER 17, 2020
The IT giant pointed out that major events like elections and COVID-19 represent opportunities for threat actors. During the last summer, Google observed threat actors from China, Russia, and Iran targeting pharmaceutical companies and researchers involved in the development of a vaccine. . Tbps, the largest DDoS attack of ever.

















Let's personalize your content