IBM Cloud inactive identities: Ideas for automated processing
IBM Big Data Hub
SEPTEMBER 29, 2023
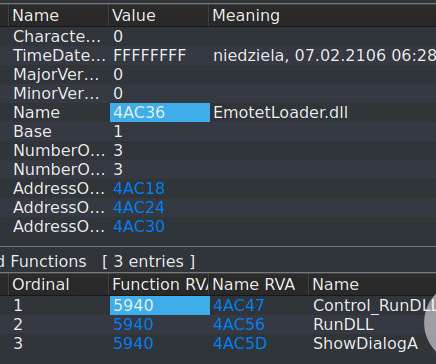
Regular cleanup is part of all account administration and security best practices, not just for cloud environments. Inactive identities pose a security risk because they might be no longer maintained and be easier to attack. Some readers provided feedback and asked on how to proceed and act on identified inactive identities.




























Let's personalize your content