Survey reports skills in technology and Digital Preservation will be most desired in the next five years
Preservica
FEBRUARY 16, 2023
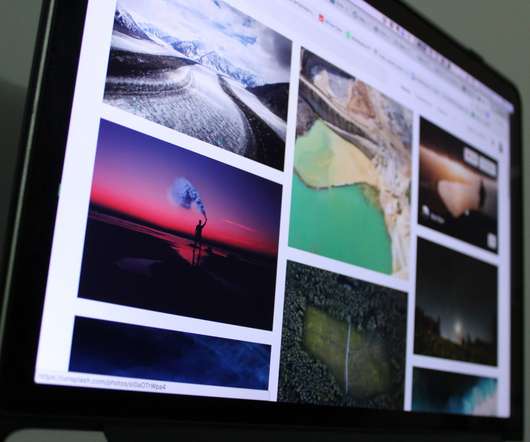
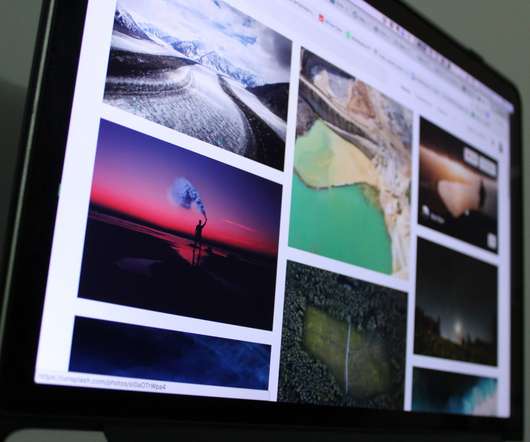
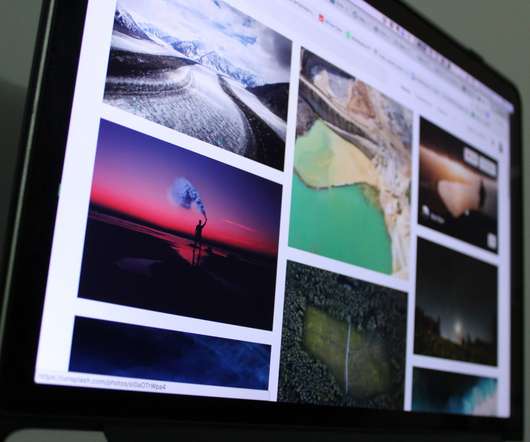
Ithaka S+R recently published a report based on findings from A*CENSUS II Archives Administrators Survey , which gathered data from 746 of the most senior archives leaders and decision-makers.


























Let's personalize your content