To Make the Internet of Things Safe, Start with Manufacturing
Thales Cloud Protection & Licensing
SEPTEMBER 11, 2018
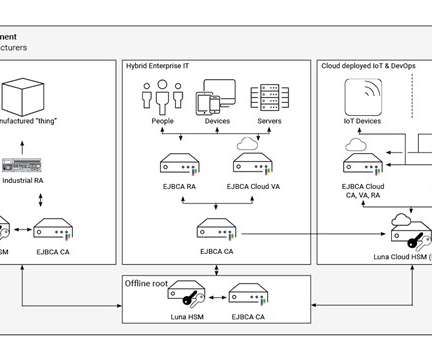
As an increasing number of connected devices are deployed within IoT ecosystems, enterprises need to identify and authenticate them. Typically, when they are manufactured, IoT devices receive their initial identity in the form of a “digital birth certificate.” Controlling Production Runs. This leads us to the second step.
















Let's personalize your content