Experts warn of a surge in NetSupport RAT attacks against education and government sectors
Security Affairs
NOVEMBER 21, 2023
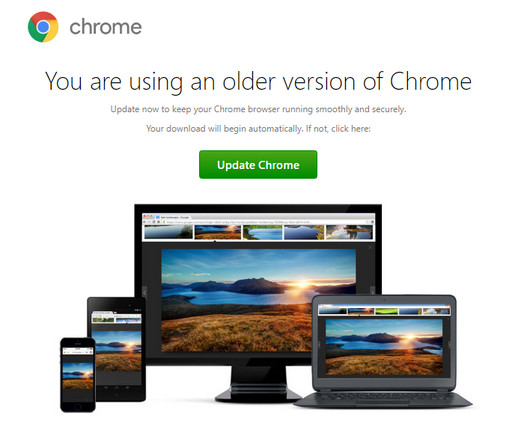
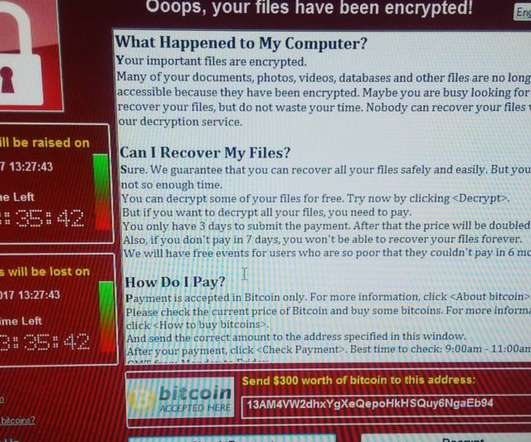
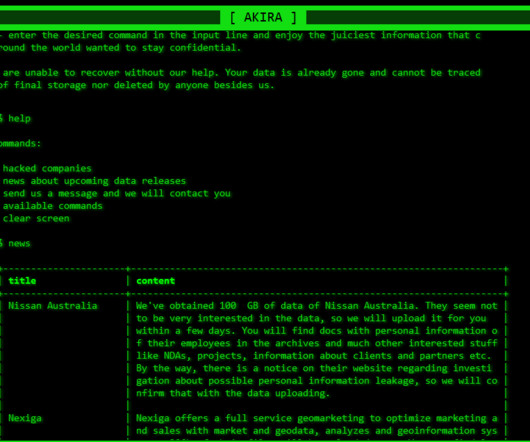
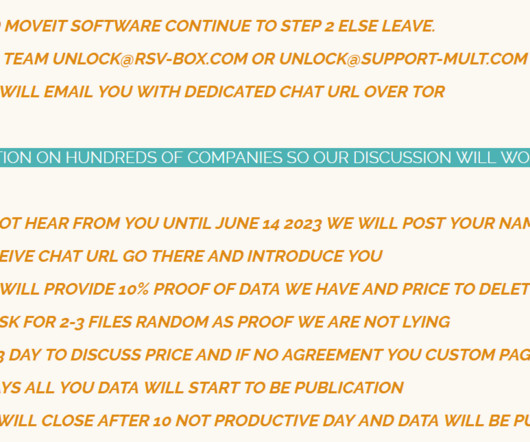
Experts warn of a surge in NetSupport RAT attacks against education, government, and business services sectors. The most impacted sectors are education, government, and business services. These infected websites host a PHP script which displays a seemingly authentic update. implacavelvideos[.]com).











































Let's personalize your content