LookingGlass Cyber Solutions: Threat Intelligence Review
eSecurity Planet
FEBRUARY 10, 2023
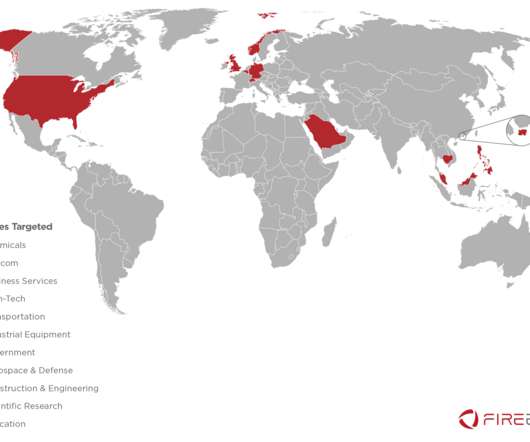
This article provides more in-depth information on the product and its features. Markets and Use Cases LookingGlass is suitable for all verticals, with particular uptake when utilizing it in a third-party risk monitoring capacity. For a comparison with other TIP products, see our complete list of top threat intelligence companies.





























Let's personalize your content