StrelaStealer targeted over 100 organizations across the EU and US
Security Affairs
MARCH 25, 2024
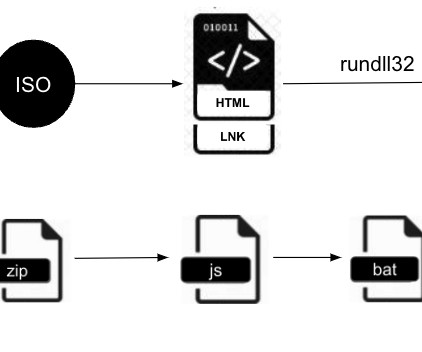
The campaign targeted organizations in many sectors, including the high-tech, finance, legal services and manufacturing industries. Upon downloading and opening the archive, a JScript file is dropped onto the system. “The JScript file then drops a Base64-encrypted file and a batch file. . ” concludes the report.





















Let's personalize your content