Info stealer attacks target macOS users
Security Affairs
APRIL 1, 2024
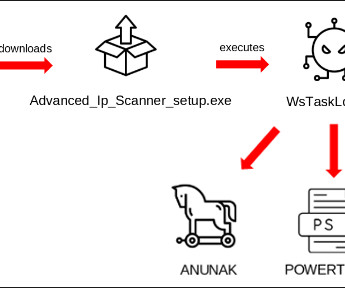
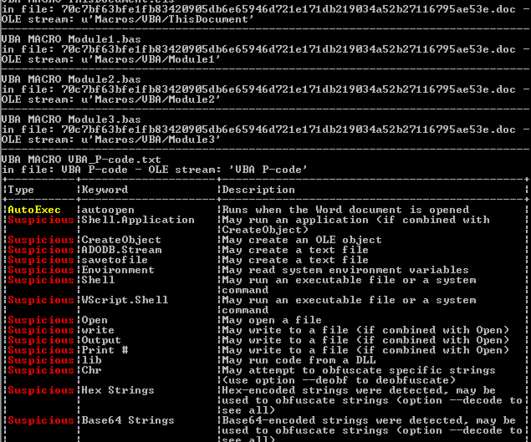
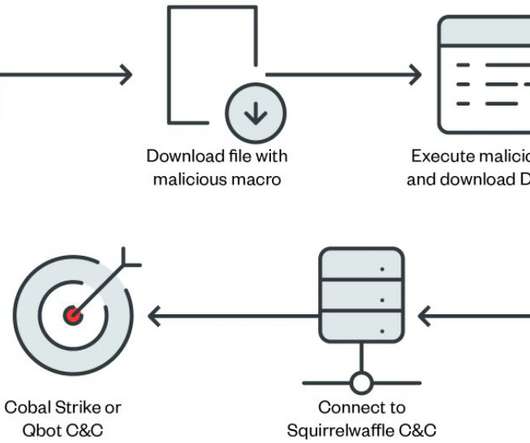
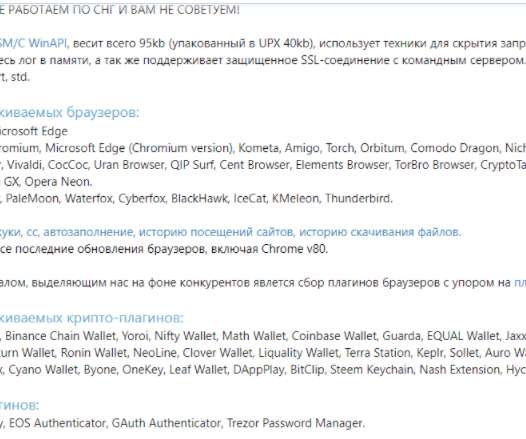
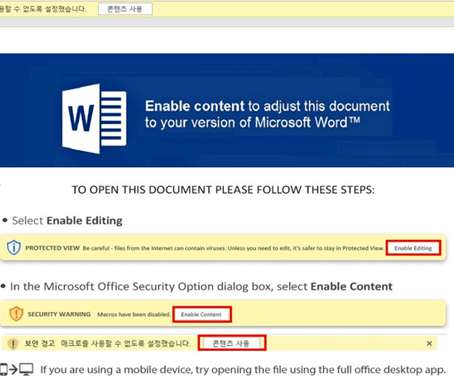
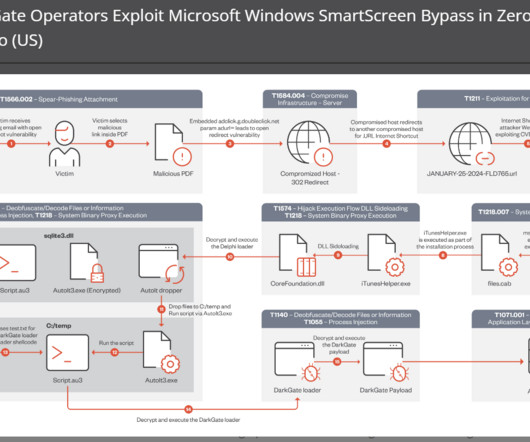
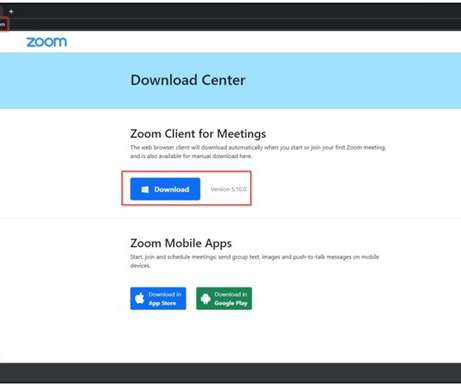
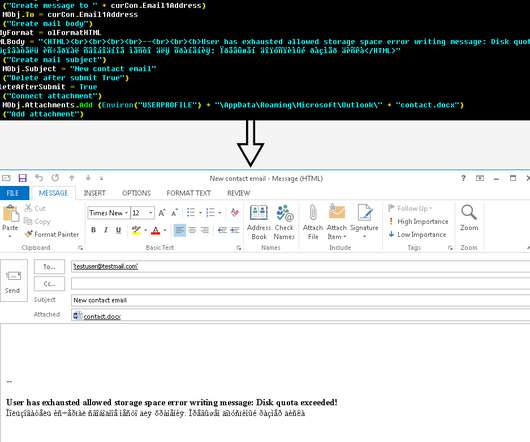
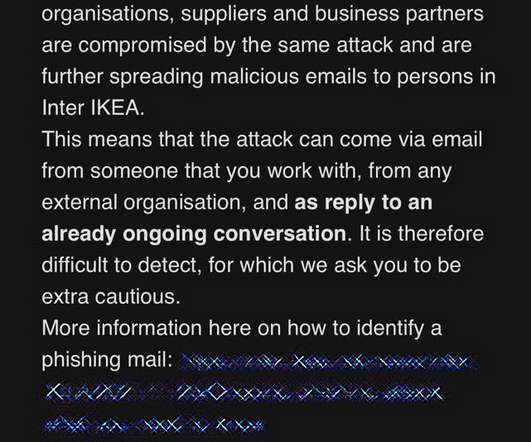
Experts warn of info stealer malware, including Atomic Stealer, targeting Apple macOS users via malicious ads and rogue websites. Jamf Threat Labs researchers analyzed info stealer malware attacks targeting macOS users via malicious ads and rogue websites. The search engine proposed a malicious site aricl[.]net




















Let's personalize your content