AI Governance: Why our tested framework is essential in an AI world
Collibra
AUGUST 14, 2023
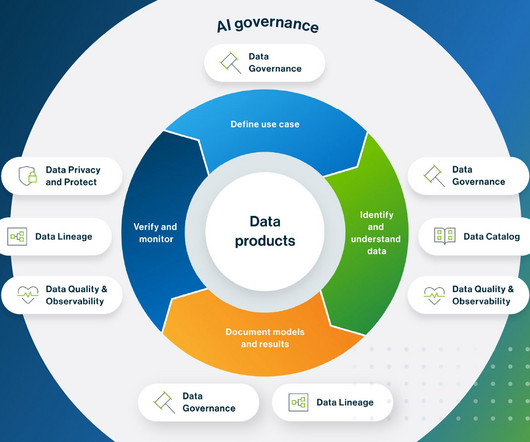
If you’re in financial services, maybe you’re considering how to incorporate AI into fraud detection, or personalized customer service, denial explanations or financial reporting. Remember, your model analysis is an effort to get some initial results from the model before you move into production.















Let's personalize your content