REvil ransomware gang hacked Acer and is demanding a $50 million ransom
Security Affairs
MARCH 20, 2021
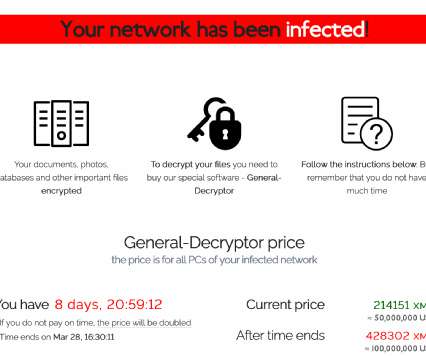
Taiwanese multinational hardware and electronics corporation Acer was victim of a REvil ransomware attack, the gang demanded a $50,000,000 ransom. Taiwanese computer giant Acer was victim of the REvil ransomware attack, the gang is demanding the payment of a $50,000,000 ransom, the largest one to date. billion in revenue.
















Let's personalize your content