TeamTNT is back and targets servers to run Bitcoin encryption solvers
Security Affairs
SEPTEMBER 19, 2022
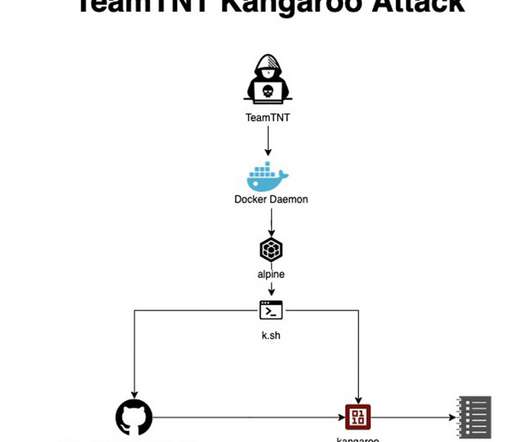
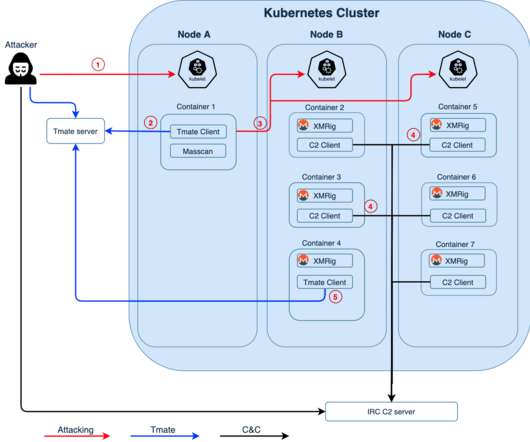
The TeamTNT botnet is a crypto-mining malware operation that has been active since April 2020 and targets Docker installs. ” reads the analysis published by AquaSec. “Breaking the cryptographic encryption is considered “Mission: Impossible”. be on IP 93[.]95[.]229[.]203).” ” continue the experts.





















Let's personalize your content