Zscaler Buys Airgap Networks to Fuel Segmentation in IoT, OT
Data Breach Today
APRIL 11, 2024
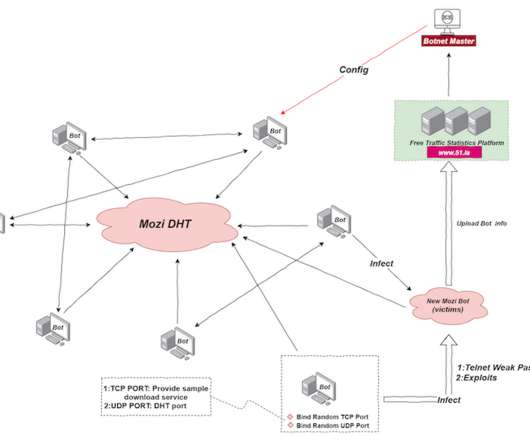
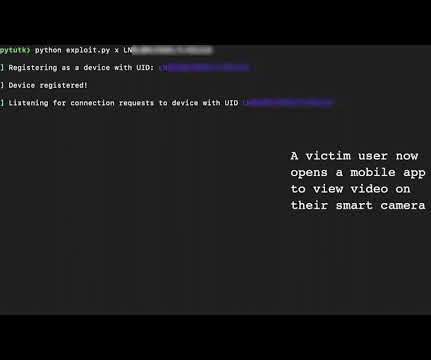
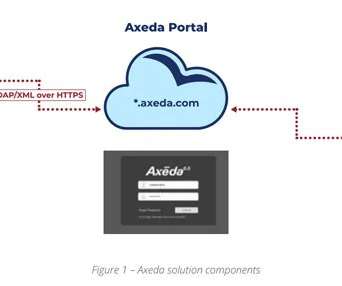
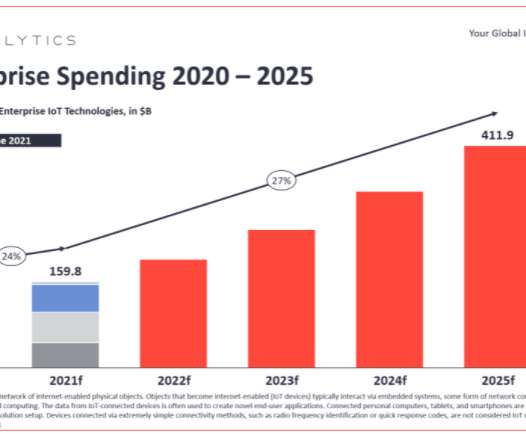
Deal Will Thwart Lateral Movement of Malicious Traffic Inside of Corporate Networks Zscaler purchased an agentless segmentation startup founded by longtime Juniper Networks executives to dynamically control access to critical infrastructure based on identity and context.










































Let's personalize your content