Russia-linked APT28 and crooks are still using the Moobot botnet
Security Affairs
MAY 3, 2024
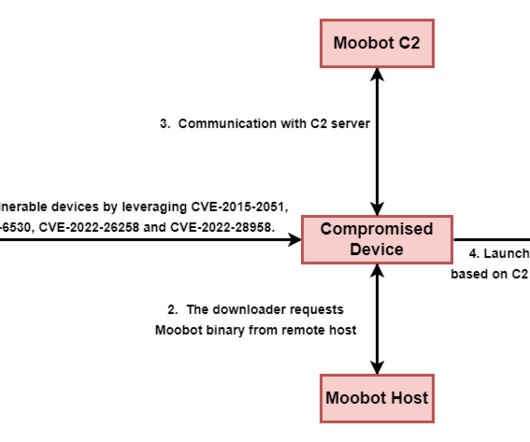
The discovery underscores significant interest among different threat actors in compromising internet-facing routers. Pawn Storm most likely easily brute forced the credentials of the backdoored SSH servers and thus gained access to a pool of EdgeRouter devices they could abuse for various purposes.” ” reported Trend Micro.

















Let's personalize your content