FBI Hacker Dropped Stolen Airbus Data on 9/11
Krebs on Security
SEPTEMBER 13, 2023
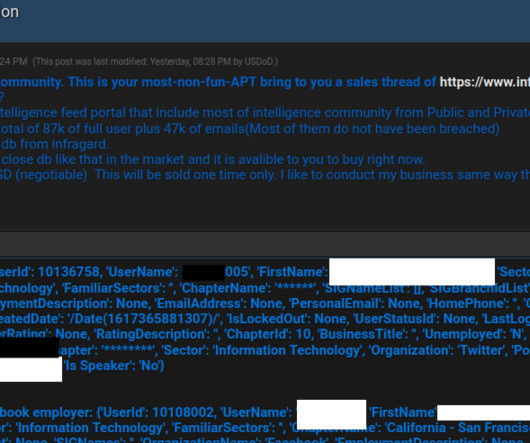
11, 2023, USDoD resurfaced after a lengthy absence to leak sensitive employee data stolen from the aerospace giant Airbus , while promising to visit the same treatment on top U.S. USDoD claimed they grabbed the data by using passwords stolen from a Turkish airline employee who had third-party access to Airbus’ systems.
















Let's personalize your content