Capital One Breach Conviction Exposes Scale of Cloud Entitlement Risk
Dark Reading
AUGUST 2, 2022
To protect against similar attacks, organizations should focus on bringing cloud entitlements and configurations under control.

Dark Reading
AUGUST 2, 2022
To protect against similar attacks, organizations should focus on bringing cloud entitlements and configurations under control.

Data Breach Today
AUGUST 2, 2022
Florida Urgent Care Center Says Incident Involved Billing Vendor PracticeMax A Florida operator of urgent care clinics recently reported to federal regulators a health data breach affecting more than 258,000 individuals tied to a vendor's ransomware attack in May 2021. Why did it take so long to determine that the incident resulted in breach of protected health information?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Krebs on Security
AUGUST 2, 2022
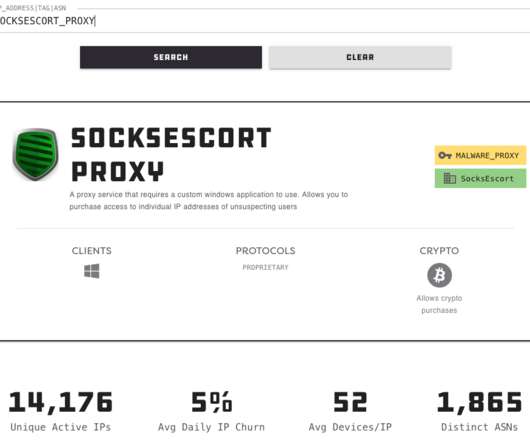
With the recent demise of several popular “proxy” services that let cybercriminals route their malicious traffic through hacked PCs, there is now something of a supply chain crisis gripping the underbelly of the Internet. Compounding the problem, several remaining malware-based proxy services have chosen to block new registrations to avoid swamping their networks with a sudden influx of customers.

Data Breach Today
AUGUST 2, 2022
Insurer Says OneTouchPoint Was a Subcontractor Health insurer Aetna ACE reported to federal regulators a health data breach affecting nearly 326,000 individuals tied to an apparent ransomware incident involving OneTouchPoint, a subcontractor that provides printing and mailing services to one of the insurer's vendors.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Data Protection Report
AUGUST 2, 2022
In our previous publication , we discussed the legal obligations and procedural considerations surrounding maintaining records of privacy incidents. While the specific obligations vary by jurisdiction, maintaining some form of a record that tracks privacy incidents is a statutory obligation for private-sector organizations subject to Quebec, Alberta, or federal laws.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

eSecurity Planet
AUGUST 2, 2022
Linux malware is skyrocketing and now surpasses both macOS and Android, according to a new report, suggesting that cybercriminals are increasingly targeting the open source operating system. The Atlas VPN report said the number of new Linux malware samples collected soared by 646% from the first half of 2021 to the first half of 2022, from 226,334 samples to nearly 1.7 million.

Data Breach Today
AUGUST 2, 2022
Acquisition to Offer Netskope Customers the Entire SASE Stack in One Place With its acquisition of Infiot, Netskope now carries both the networking and security technology needed to build a Secure Access Service Edge architecture following. The acquisition of Infiot's platform will allow Netskope customers to address both traditional and emerging SD-WAN use cases.

Data Protection Report
AUGUST 2, 2022
The Transportation Security Administration (“TSA”) announced on July 21, 2022 that it is transitioning to a less prescriptive and more result-based approach in its revised emergency cybersecurity directive for critical gas and liquid pipeline companies. The Security Directive Pipeline-2021-02C (“ SD02C ”), effective July 27, 2022, represents a significant departure from the highly prescriptive requirements set forth in its predecessor directives (SD 2021-02A and SD 2021-02B) issued by the TSA l

Data Breach Today
AUGUST 2, 2022
Attacker Exploited Bug Introduced During 'Routine Upgrade' Attackers drained crypto assets worth nearly $200 million on Monday from cross-chain bridge Nomad, a "security-first cross-chain messaging protocol." Experts say the attack occurred after Nomad updated its smart contracts and inadvertently made it easy to spoof transactions.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Schneier on Security
AUGUST 2, 2022
TheMarkup has an extensive analysis of connected vehicle data and the companies that are collecting it. The Markup has identified 37 companies that are part of the rapidly growing connected vehicle data industry that seeks to monetize such data in an environment with few regulations governing its sale or use. While many of these companies stress they are using aggregated or anonymized data, the unique nature of location and movement data increases the potential for violations of user privacy.

Data Breach Today
AUGUST 2, 2022
Trading Platform Had Poor Cybersecurity and Anti-Money Laundering Controls Cryptocurrency trading platform Robinhood Crypto will pay $30 million to the state of New York after an investigation revealed deficiencies in its cybersecurity and anti-money laundering programs. The company will also retain an independent consultant who will monitor remediation efforts.

Threatpost
AUGUST 2, 2022
DMARC analysis by Proofpoint shows that institutions in the U.S. have among some of the poorest protections to prevent domain spoofing and lack protections to block fraudulent emails.

Security Affairs
AUGUST 2, 2022
VMware patched a critical authentication bypass security flaw, tracked as CVE-2022-31656, impacting local domain users in multiple products. VMware has addressed a critical authentication bypass security flaw, tracked as CVE-2022-31656, impacting local domain users in multiple products. An unauthenticated attacker can exploit the vulnerability to gain admin privileges. “A malicious actor with network access to the UI may be able to obtain administrative access without the need to authentic

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Collibra
AUGUST 2, 2022
A data governance council is a governing body for strategizing data governance programs, raising awareness of its importance, approving enterprise data policies and standards, prioritizing related projects, and enabling ongoing support. The data governance council empowers all to create value from data assets while complying with security and privacy.

Dark Reading
AUGUST 2, 2022
From adopting zero-trust security models to dynamic environments to operating under an "assumed breach" mentality, here are ways IT departments can reduce vulnerabilities as they move deliberately to become more secure.
Security Affairs
AUGUST 2, 2022
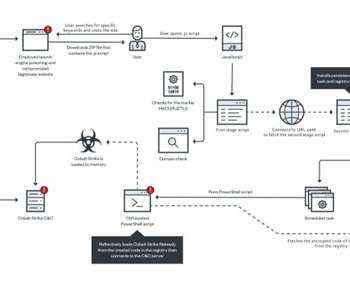
Gootkit access-as-a-service (AaaS) malware is back with tactics and fileless delivery of Cobalt Strike beacons. Gootkit runs on an access-a-as-a-service model, it is used by different groups to drop additional malicious payloads on the compromised systems. Gootkit has been known to use fileless techniques to deliver threats such as the SunCrypt , and REvil (Sodinokibi) ransomware, Kronos trojans, and Cobalt Strike.

Hanzo Learning Center
AUGUST 2, 2022
Ediscovery and compliance are no longer reactive endeavors. Organizations must be proactive in order to mitigate legal and regulatory risk, and waiting for the perfect API for all of your data sources isn’t a sustainable option. Legal and compliance teams need a solution to capture the required data from the myriad and ever-growing onslaught of SaaS applications in today’s enterprise technology stack.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.
Security Affairs
AUGUST 2, 2022
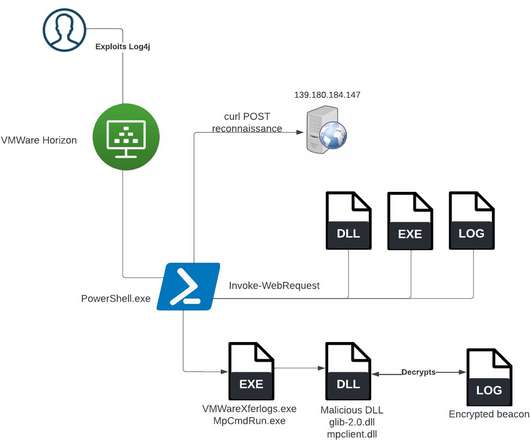
An affiliate of the LockBit 3.0 RaaS operation has been abusing the Windows Defender command-line tool to deploy Cobalt Strike payloads. During a recent investigation, SentinelOne researchers observed threat actors associated with the LockBit 3.0 ransomware-as-a-service (RaaS) operation abusing the Windows Defender command line tool MpCmdRun.exe to decrypt and load Cobalt Strike payloads.

Dark Reading
AUGUST 2, 2022
Attackers are turning to stolen credentials and posing as trusted applications to socially engineer victims, according to Google study of malware submitted to VirusTotal.
Security Affairs
AUGUST 2, 2022
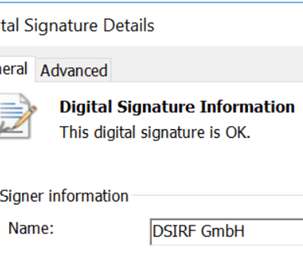
Austria is investigating a report that an Austrian firm DSIRF developed spyware targeting law firms, banks and consultancies. At the end of July, Microsoft Threat Intelligence Center (MSTIC) and the Microsoft Security Response Center (MSRC) researchers linked a threat group known as Knotweed to an Austrian surveillance firm named DSIRF, known for using multiple Windows and Adobe zero-day exploits.

Dark Reading
AUGUST 2, 2022
Microsoft says the new tools will give security teams an attacker's-eye view of their systems and supercharge their investigation and remediation efforts.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

KnowBe4
AUGUST 2, 2022
New data about the state of cyber insurance shows that given the current loss ratios by insurers – and the reasons behind those losses – will result in higher premiums for the foreseeable future.

Dark Reading
AUGUST 2, 2022
The campaign uses adversary-in-the-middle techniques to bypass multifactor authentication, evade detection.

KnowBe4
AUGUST 2, 2022
After a few notifications of a potential problem with Experian by his readership, Brian Krebs and team checked out Experian’s account signup process and found some disturbing news.

Dark Reading
AUGUST 2, 2022
With over 323 million users of dating apps worldwide, study finds location spoofing is a threat to user trust and safety.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

KnowBe4
AUGUST 2, 2022
The 2022 KnowBe4 Women’s Day Survey interviewed more than 200 women from across the technology industry in South Africa to find out more about how they perceive the industry, the gender gap and discrimination. The survey focused on some of the key challenges traditionally experienced by women in the IT and technology sectors and interviewed women ranging in age from 25-54.

Dark Reading
AUGUST 2, 2022
New finding comes amid report of overall surge in threats targeting mobile and IoT devices over the past year.

WIRED Threat Level
AUGUST 2, 2022
Roman Sterlingov, accused of laundering $336 million, is proclaiming his innocence—and challenging a key investigative tool.
Let's personalize your content