Surveillance vendor exploited Samsung phone zero-days
Security Affairs
NOVEMBER 9, 2022
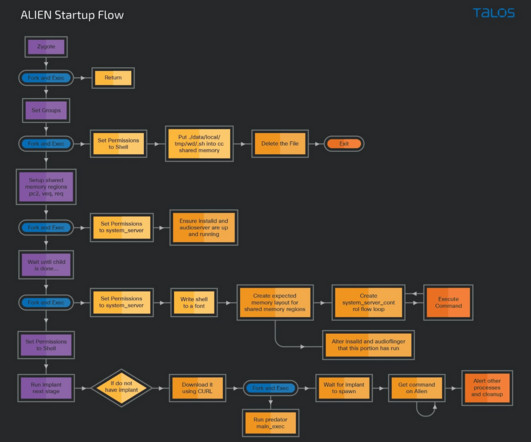
Google Project Zero researchers reported that a surveillance vendor is using three Samsung phone zero-day exploits. Google Project Zero disclosed three Samsung phone vulnerabilities, tracked as CVE-2021-25337, CVE-2021-25369 and CVE-2021-25370, that have been exploited by a surveillance company.

















Let's personalize your content