Chinese Hackers Stole an NSA Windows Exploit in 2014
Schneier on Security
MARCH 4, 2021
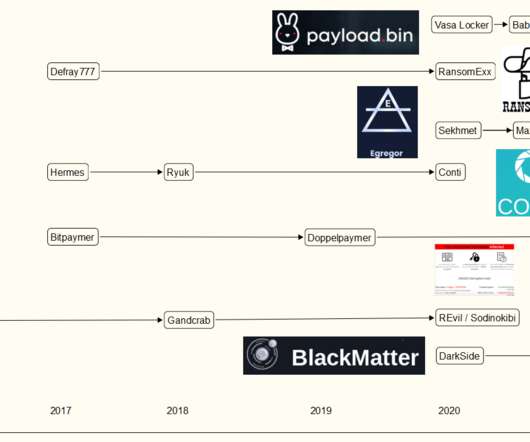
Check Point has evidence that (probably government affiliated) Chinese hackers stole and cloned an NSA Windows hacking tool years before (probably government affiliated) Russian hackers stole and then published the same tool. This allows someone with a foothold on a machine to commandeer the whole box.























Let's personalize your content