From iPhone to NT AUTHORITYSYSTEM – exploit ‘Printconfig’ dll with a real-world example
Security Affairs
DECEMBER 15, 2019
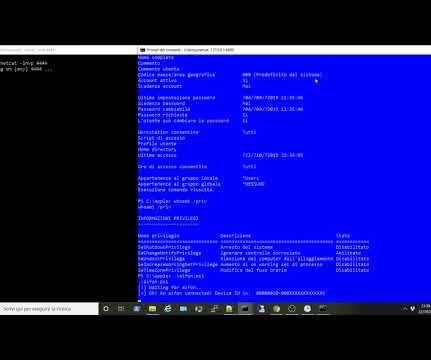
From iPhone to NT AUTHORITYSYSTEM – As promised in my previous post , I will show you how to exploit the “Printconfig” dll with a real world example. He can define himself “security enthusiast”, interested in all emerging technologies in offensive and defensive security. But what does Apple’s iPhone have to do with it??



































Let's personalize your content