From iPhone to NT AUTHORITYSYSTEM – exploit ‘Printconfig’ dll with a real-world example
Security Affairs
DECEMBER 15, 2019
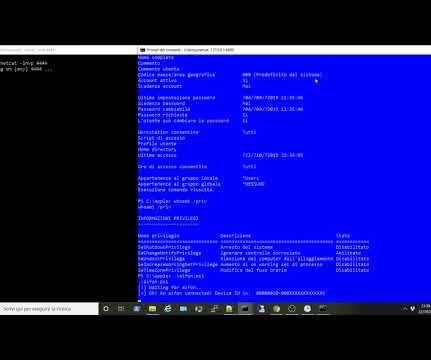
From iPhone to NT AUTHORITYSYSTEM – As promised in my previous post , I will show you how to exploit the “Printconfig” dll with a real world example. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->. Boundary conditions.













































Let's personalize your content