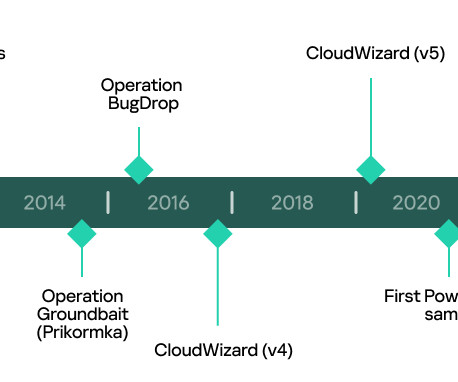
A deeper insight into the CloudWizard APT’s activity revealed a long-running activity
Security Affairs
MAY 23, 2023
A deeper analysis revealed that the threat actor CloudWizard has been linked to an activity cluster that dates back to May 2016 that was tracked by ESET researchers as Operation Groundbait. Further analysis revealed that the actor behind the above operations has been active since at least 2008. ” We are in the final!



















Let's personalize your content