Actively exploited Windows Mark-of-the-Web zero-day received an unofficial patch
Security Affairs
OCTOBER 31, 2022
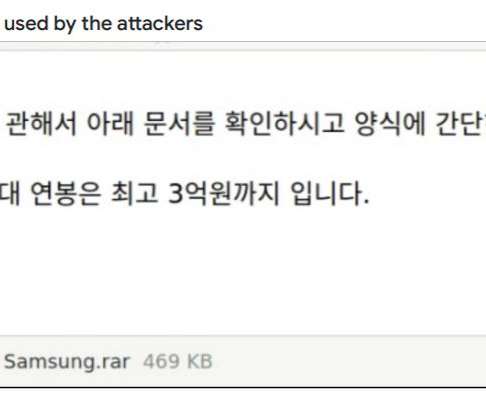
“Patrick works at HP Wolf Security where they analyzed the Magniber Ransomware and wrote a detailed analysis of its working. In order to prevent unauthorized actions, files downloaded from the internet in Windows are tagged with a MotW flag. “You can see the effect of our micropatch in the following video.”



















Let's personalize your content