Who’s Behind the ‘Web Listings’ Mail Scam?
Krebs on Security
MARCH 23, 2020
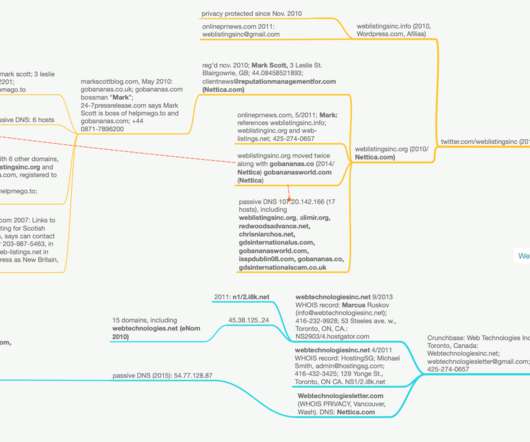
According to Farsight Security , a company that keeps historic records of which Web sites were hosted at which Internet addresses, Weblistingsinc.org was for a while hosted at the IP address 68.169.45.65 Historic WHOIS data from Domaintools.com says Webtechnologiesinc.net was registered in 2013 to a Marcus Ruskov in Toronto.


















Let's personalize your content