Iran's Military Reportedly Backs Ransomware Campaign
Data Breach Today
MAY 4, 2021
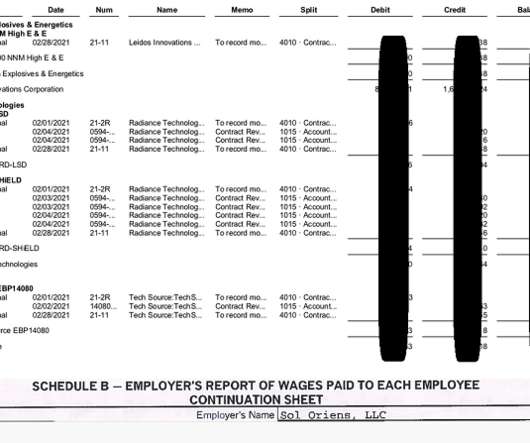
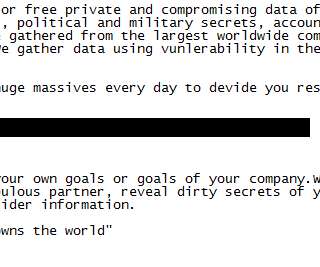
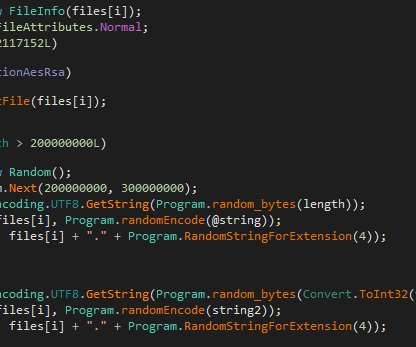
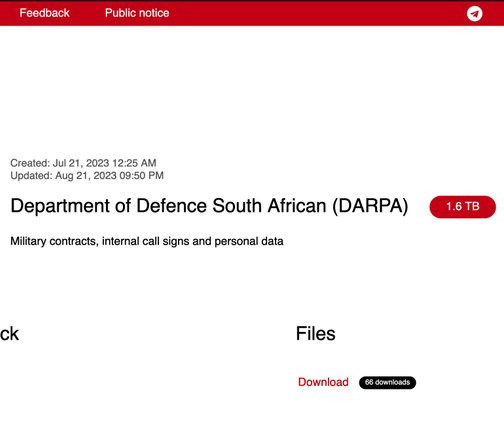
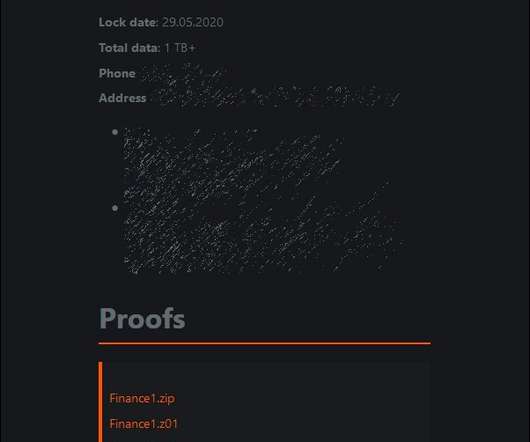
Iran's Islamic Revolutionary Guard Corps was behind a ransomware campaign that used a contracting company called "Emen Net Pasargard" to target more than a dozen organizations, according to the security firm Flashpoint. Could Cyberespionage Be Campaign's Real Purpose? But could cyberespionage be the campaign's true mission?






























Let's personalize your content