Pro-Ukraine attackers compromise Docker images to launch DDoS attacks on Russian sites
Security Affairs
MAY 4, 2022
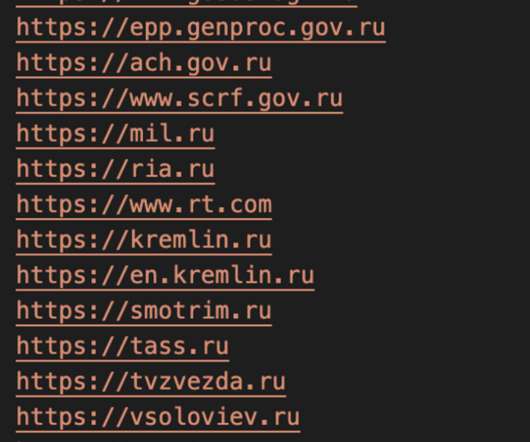
Pro-Ukraine hackers, likely linked to Ukraine IT Army , are using Docker images to launch distributed denial-of-service (DDoS) attacks against a dozen websites belonging to government, military, and media. “Container and cloud-based resources are being abused to deploy disruptive tools. ” reported Crowdstrike.



















Let's personalize your content