China-linked APT10 Target Taiwan’s financial trading industry
Security Affairs
FEBRUARY 22, 2022
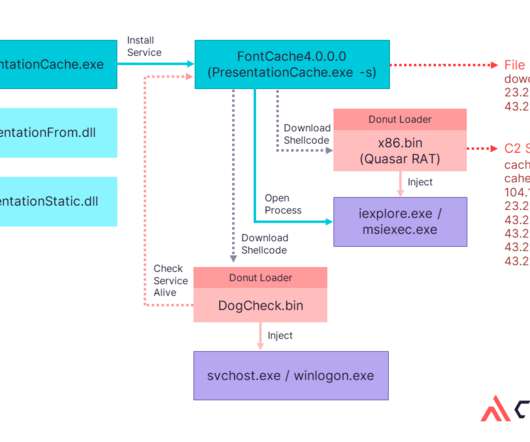
The group (also known as Cicada, Stone Panda , MenuPass group, Bronze Riverside, and Cloud Hopper ) has been active at least since 2009, in April 2017 experts from PwC UK and BAE Systems uncovered a widespread hacking campaign, tracked as Operation Cloud Hopper , targeting managed service providers (MSPs) in multiple countries worldwide.


















Let's personalize your content