Shoemaker Ecco leaks over 60GB of sensitive data for 500+ days
Security Affairs
DECEMBER 21, 2022
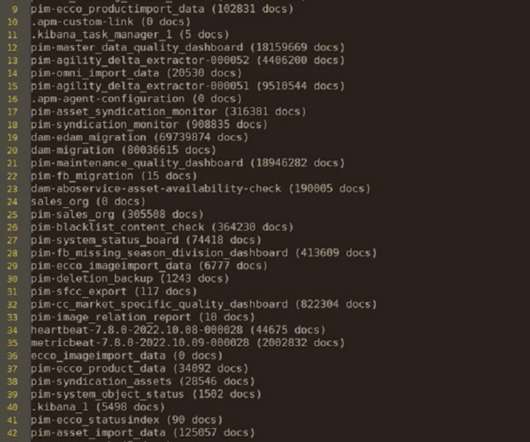
CyberNews researchers reported that Ecco, a global shoe manufacturer and retailer, exposed millions of documents. Ecco, a global shoe manufacturer and retailer, exposed millions of documents. For example, a directory named sales_org contained over 300,000 documents. Original post @ [link].
















Let's personalize your content