P2P Weakness Exposes Millions of IoT Devices
Krebs on Security
APRIL 26, 2019
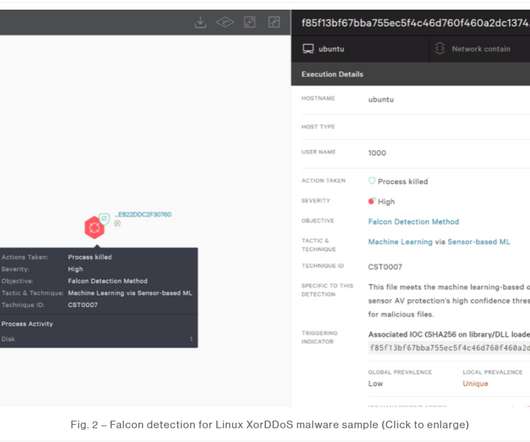
A map showing the distribution of some 2 million iLinkP2P-enabled devices that are vulnerable to eavesdropping, password theft and possibly remote compromise, according to new research. If the code stamped on your IoT device begins with one of these, it is vulnerable.












































Let's personalize your content