Threat actors are actively exploiting Zerologon flaw, Microsoft warns
Security Affairs
OCTOBER 30, 2020
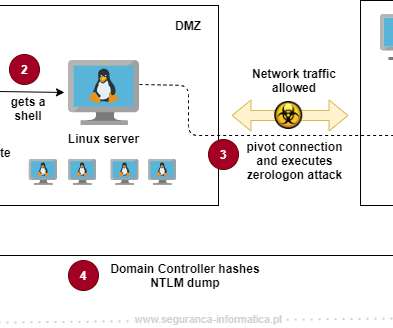
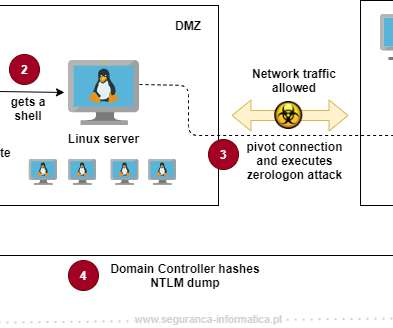
An attacker could also exploit the flaw to disable security features in the Netlogon authentication process and change a computer’s password on the domain controller’s Active Directory. FIND which devices are making vulnerable connections by monitoring event logs. Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->.













Let's personalize your content