TeamTNT is back and targets servers to run Bitcoin encryption solvers
Security Affairs
SEPTEMBER 19, 2022
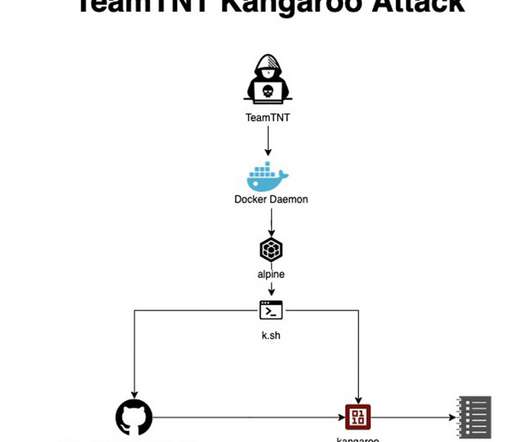
The TeamTNT botnet is a crypto-mining malware operation that has been active since April 2020 and targets Docker installs. The activity of the TeamTNT group has been detailed by security firm Trend Micro, but in August 2020 experts from Cado Security discovered that botnet is also able to target misconfigured Kubernetes installations.


























Let's personalize your content