Ukraine’s GUR hacked the Russian Ministry of Defense
Security Affairs
MARCH 4, 2024
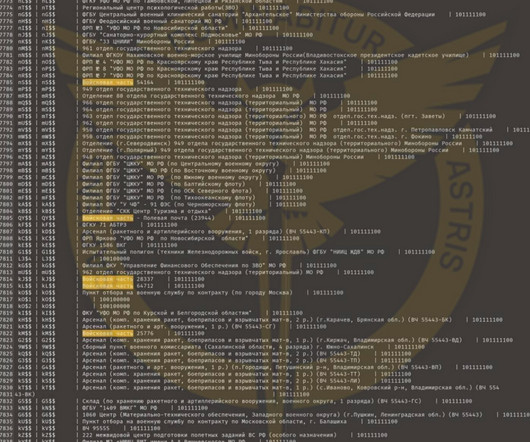
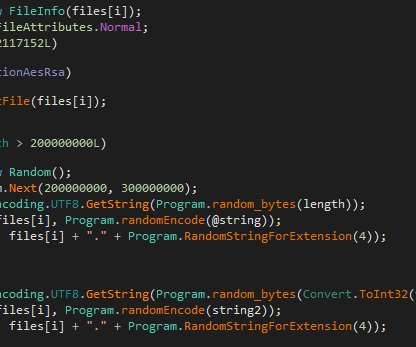
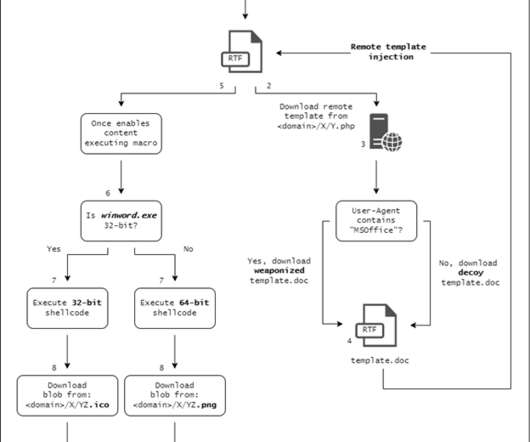
Stolen documents include: confidential documents, including orders and reports circulated among over 2000 structural units of the Russian military service. software used by the Russian Ministry of Defense to encrypt and protect its data. ” reads the press release published by Ukraine’s GUR.

































Let's personalize your content