DearCry Ransomware Targets Unpatched Exchange Servers
Data Breach Today
MARCH 12, 2021
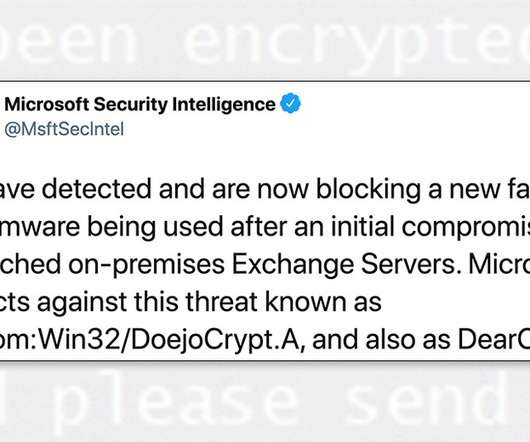
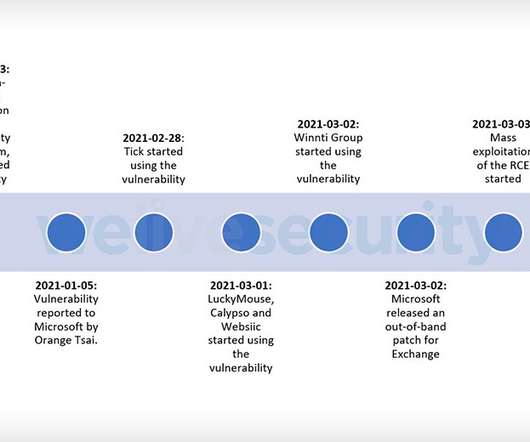
On-Premises Exchange Servers May Have Been Hacked Since January, Experts Warn Attackers wielding DearCry - aka DoejoCrypt - ransomware have begun to exploit the serious proxy-logon flaw in unpatched versions of Microsoft Exchange running on premises. The vulnerability is one of four zero-day flaws patched last week by Microsoft, which APT attackers began exploiting in January.





































Let's personalize your content