Indian Payment Platform JustPay Breached
Data Breach Today
JANUARY 5, 2021
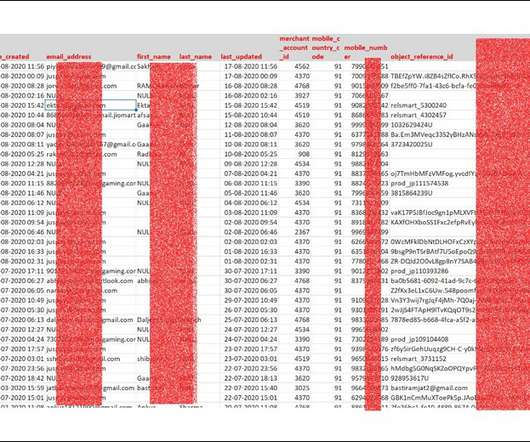
Security Researcher Says Leaked Data Offered for Sale on Darknet JustPay, an Indian online payment platform, acknowledged Monday that it sustained a major breach of customer data in August. The announcement came a day after an independent security researcher reported that data on millions of JustPay customers had been offered for sale on a darknet forum.




































Let's personalize your content