Software Supply Chain Concerns Reach C-Suite
Dark Reading
JULY 19, 2022
Major supply chain attacks have had a significant impact on software security awareness and decision-making, with more investment planned for monitoring attack surfaces.

Dark Reading
JULY 19, 2022
Major supply chain attacks have had a significant impact on software security awareness and decision-making, with more investment planned for monitoring attack surfaces.

Data Breach Today
JULY 19, 2022
US Seeking To Shut Out Huawei and ZTT From Domestic Networks A $2 billion fund to root out equipment from Chinese manufacturers Huawei and ZTE operating within small and rural U.S. telecoms isn't enough to cover costs, the Federal Communications Commission informed Congress. The program's full cost is closer to $5 billion, wrote FCC Chair Jessica Rosenworcel.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Dark Reading
JULY 19, 2022
A GPS device from MiCODUS has six security bugs that could allow attackers to monitor 1.5 million vehicles that use the tracker, or even remotely disable vehicles.

Data Breach Today
JULY 19, 2022
Walmart-Owned Cleartrip Apparently Suffered a Data Breach Popular Indian online travel website Cleartrip is investigating a "security anomaly" amid signs that it suffered a major data breach. "Appropriate legal action and recourse are being evaluated and steps are being taken," it says. Cleartrip is part of Walmart-controlled e-commerce firm Flipkart.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

KnowBe4
JULY 19, 2022
The latest iteration in Copyright Claim scams is an evolution of this repeated attack method that has proven to get the attention – and response – of victims over the last few years.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
Security Affairs
JULY 19, 2022
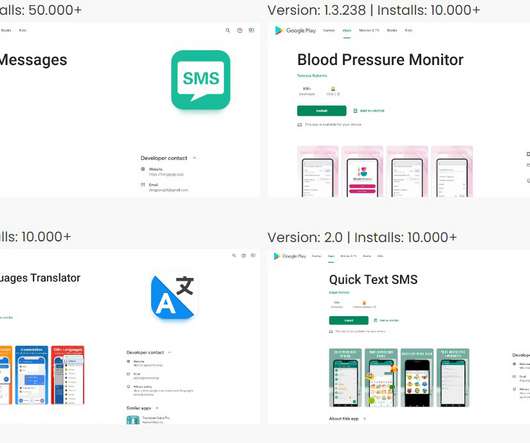
Google blocked dozens of malicious apps from the official Play Store that were spreading Joker, Facestealer, and Coper malware families. Google has removed dozens of malicious apps from the official Play Store that were distributing Joker, Facestealer, and Coper malware families. Researchers from security firms Pradeo discovered multiple apps spreading the Joker Android malware.
Data Breach Today
JULY 19, 2022
Feds Clawed Back Money Paid in 'Maui' Ransomware Assaults The U.S. Justice Department clawed back $500,000 from North Korean-government-sponsored cyberattackers who launched Maui ransomware assaults on the U.S. healthcare sector. Healthcare ransomware attacks have soared over the past two years, and the sector is among those most likely to pay a ransom.
eSecurity Planet
JULY 19, 2022
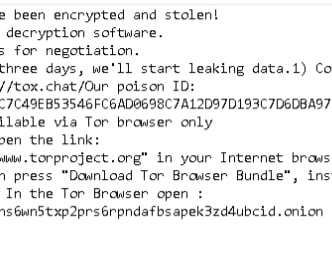
Discovered by malware hunter JAMESWT on Twitter, Lilith is ransomware designed to lock Windows machines. The malware exfiltrates data before encrypting the targeted devices to provide additional means of extortion. The ransom note contains the following ultimatum and instructions: Victims have three days to contact the threat actors on a hidden Onion website to pay the ransom.

Data Breach Today
JULY 19, 2022
The Combined ePlus-Future Com Will Help Customers Marry Cloud-Based SIEM With SOAR The company ePlus has purchased Future Com to strengthen its security operations strategy and support of managed services. The deal will allow ePlus to help customers evolve their security operations teams from correlating and analyzing logs to delivering advanced capabilities like threat hunting.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Hanzo Learning Center
JULY 19, 2022
When it comes to ediscovery and compliance, APIs can give users the ability to use 3rd party solutions to preserve, collect, and even cull data housed in a SaaS application; however, functionality is still limited to what the API is built to communicate. Even if an application has an API available, its design is often focused on the modification of objects and data rather than the creation of a consumable, universal format expected by legal and compliance teams.

Data Breach Today
JULY 19, 2022
American Cybersecurity Agency Envisions a Global Role The U.S. Cybersecurity and Infrastructure Security Agency will open a London office as a first step to building an international presence it hopes will result in more threat indicator data, improved international cybersecurity and more foreign governments adopting similar cybersecurity policies.

Security Affairs
JULY 19, 2022
The U.S. FBI has warned of crooks developing malicious cryptocurrency-themed apps to steal crypto assets from the users. The U.S. Federal Bureau of Investigation (FBI) has warned of crooks creating malicious cryptocurrency-themed apps to steal crypto assets from investors. Crooks contact US investors claiming to offer legitimate cryptocurrency investment services, and attempt to trick them into downloading fraudulent mobile apps that they have created.

Data Breach Today
JULY 19, 2022
Future quantum computers will decrypt encrypted data, so businesses feel pressure to find quantum-resistant security solutions for data transmission. Wells Fargo Bank's Peter Bordow discusses the state of quantum computing, approaches to quantum security, and privacy-enhancing technologies.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

The Security Ledger
JULY 19, 2022
An “everywhere,” hybrid workforce is no longer concept, but reality. But securing hybrid workplaces requires big changes to how IT security gets done, argues Jason Lee, the CISO of Zoom in this Expert Insight. The post Hybrid Work Is Here: Is Your Security Strategy Ready for It? appeared first on The Security Ledger with Paul F. Roberts. Related Stories Tapping into the Power of the Security Community The Future of Attack Surface Management: How to Prepare The Concerning Statistics About Mental

Dark Reading
JULY 19, 2022
Multiple cyber-insurance carriers have adopted act-of-war exclusions due to global political instability and are seeking to stretch the definition of war to deny coverage.

Outpost24
JULY 19, 2022
Phishing: Better Proxy than Story. 21.Jul.2022. Florian Barre. Tue, 07/19/2022 - 09:02. Fotios Liatsis, Senior Security Consultant at Outpost24. Penetration Testing. Teaser. In the last phishing blog we discussed how modern phishing works on the frontend. Read on to find out how threat actors can easily find and authenticate a suitable domain by modifying both Gophish and Evilginx to evade security controls.
Security Affairs
JULY 19, 2022
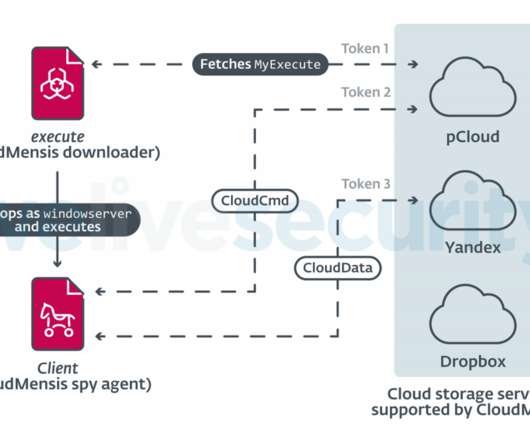
Researchers spotted previously undocumented spyware, dubbed CloudMensis, that targets the Apple macOS systems. Researchers from ESET discovered a previously undetected macOS backdoor, tracked as CloudMensis, that targets macOS systems and exclusively uses public cloud storage services as C2. The malware was designed to spy on the target systems, exfiltrate documents, acquire keystrokes, and screen captures.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

KnowBe4
JULY 19, 2022
While multi-factor authentication (MFA) significantly reduces an organization’s threat surface by making the stealing of credentials much harder, a new attack takes advantage of phone calls as the second factor.

Hunton Privacy
JULY 19, 2022
On July 6, 2022, the Better Business Bureau National Programs’ Children’s Advertising Review Unit (“CARU”) announced that it had found Outright Games in violation of the Children’s Online Privacy Protection Act (“COPPA”) and CARU’s Self-Regulatory Guidelines for Advertising and Guidelines for Children’s Online Privacy Protection. Outright Games owns and operates the Bratz Total Fashion Makeover app , which CARU determined to be a “mixed audience” child-directed app subject to COPPA and CARU’s Gu

Security Affairs
JULY 19, 2022
The Minister for Foreign Affairs of Belgium blames multiple China-linked threat actors for attacks against The country’s defense and interior ministries. The Minister for Foreign Affairs of Belgium revealed that multiple China-linked APT groups targeted the country’s defense and interior ministries. “Belgium exposes malicious cyber activities that significantly affected our sovereignty, democracy, security and society at large by targeting the FPS Interior and the Belgian Defen

Dark Reading
JULY 19, 2022
Researchers say Okta could allow attackers to easily exfiltrate passwords, impersonate other users, and alter logs to cover their tracks.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Security Affairs
JULY 19, 2022
The Council of the European Union (EU) warns of malicious cyber activities conducted by threat actors in the context of the ongoing conflict between Russia and Ukraine. The Council of the European Union (EU) warns of the risks associated with the malicious cyber activities conducted by threat actors in the context of the ongoing conflict between Russia and Ukraine.

Dark Reading
JULY 19, 2022
The gang's members have moved into different criminal activities, and could regroup once law-enforcement attention has simmered down a bit, researchers say.

Threatpost
JULY 19, 2022
Threat actors offer victims what appear to be investment services from legitimate companies to lure them into downloading malicious apps aimed at defrauding them.

Dark Reading
JULY 19, 2022
More than 311 local eateries have been breached through online ordering platforms MenuDrive, Harbortouch, and InTouchPOS, impacting 50K records — and counting.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Threatpost
JULY 19, 2022
Four newly discovered attack paths could lead to PII exposure, account takeover, even organizational data destruction.

Dark Reading
JULY 19, 2022
The Curricula platform uses behavioral science with a simplified approach to train and educate users — and marks another step forward in Huntress’ mission to secure the 99%.

WIRED Threat Level
JULY 19, 2022
Despite alerting Meta months ago, feminist groups say tens of thousands of fake accounts continue to bombard them on the platform.
Let's personalize your content