Ukrainian researcher leaked the source code of Conti Ransomware
Security Affairs
MARCH 2, 2022
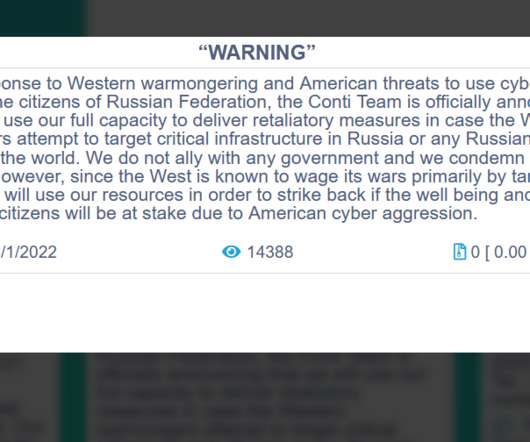
A Ukrainian researcher leaked the source for the Conti ransomware and components for the control panels. Recently a Ukrainian researcher leaked 60,694 messages internal chat messages belonging to the Conti ransomware operation after the announcement of the group of its support to Russia. He was able to access the database XMPP chat server of the Conti group. conti jabber leaks [link] — conti leaks (@ContiLeaks) February 27, 2022.









































Let's personalize your content