Zero-Day Attacks Exploit MSHTML Flaw in Microsoft Windows
Data Breach Today
SEPTEMBER 8, 2021
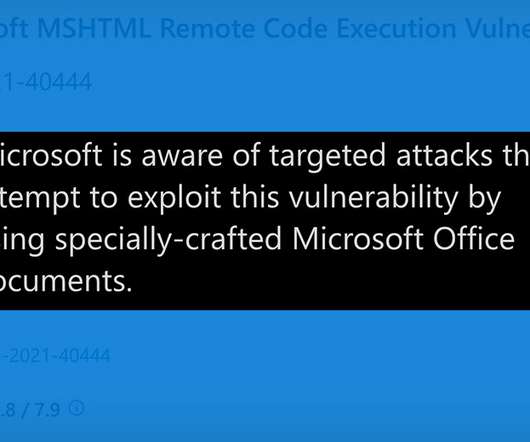
Workarounds Detailed to Block Active Attack; Microsoft Has Yet to Release Patches Attackers are actively exploiting a flaw in Microsoft Windows for which no patch is yet available. Microsoft has issued workarounds and mitigations designed to block the zero-day attack for the flaw in the MSHTML browsing engine, which is being exploited via malicious Microsoft Office documents.








































Let's personalize your content