Fraudsters Flooding Collaboration Tools With Malware
Data Breach Today
APRIL 9, 2021
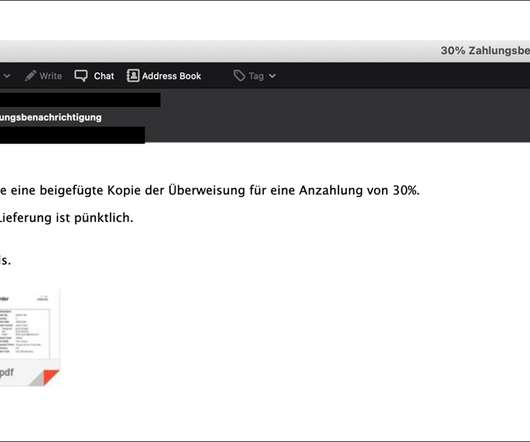
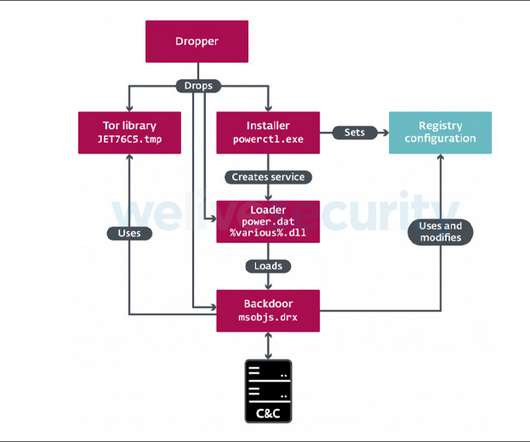
Cisco Talos: Reliance on These Tools Expands Attack Surface The increasing reliance on collaboration tools such as Slack and Discord to support those working remotely during the COVID-19 pandemic has opened up new ways for fraudsters and cybercriminals to bypass security tools and deliver malware, Cisco Talos reports.








































Let's personalize your content