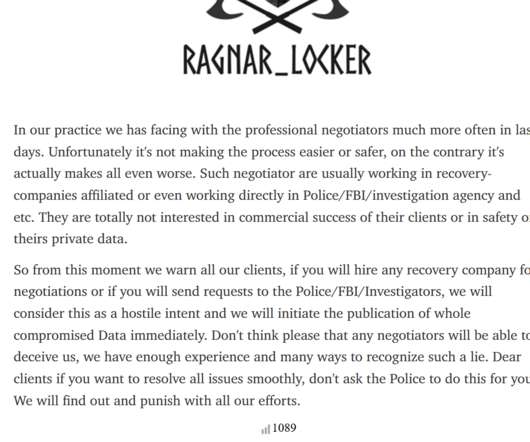
Ragnar Locker: 'Talk to Cops or Feds and We Leak Your Data'
Data Breach Today
SEPTEMBER 7, 2021
Extortionists Revert to Scareware Tactics to Pressure Victims to Avoid Negotiators The Ragnar Locker ransomware operation has been threatening to dump victims' stolen data if they contact police, private investigators or professional negotiators before paying a ransom. But as one expert notes: "Perhaps the criminals watched too many TV shows, because this isn’t how the real world works.





































Let's personalize your content