Another Takedown: NetWalker Ransomware Gang Disrupted
Data Breach Today
JANUARY 28, 2021
Authorities Seize Servers, Make 1 Arrest U.S. and Bulgarian authorities have seized servers and disrupted the infrastructure and darknet websites of the NetWalker ransomware gang. Police have also arrested one person and confiscated ransom money collected by the cybercriminal gang. The news comes the same week the Emotet botnet was disrupted.



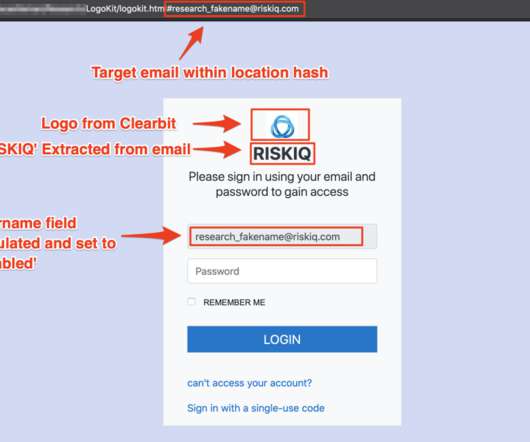



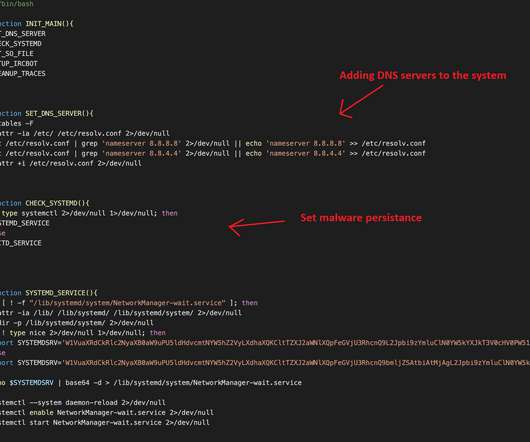





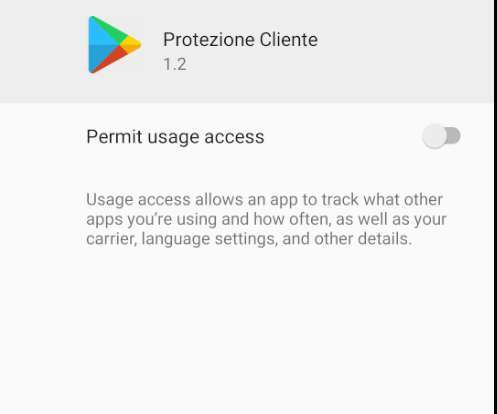



























Let's personalize your content