Microsoft Attributes MOVEit Transfer Hack to Clop Affiliate
Data Breach Today
JUNE 5, 2023
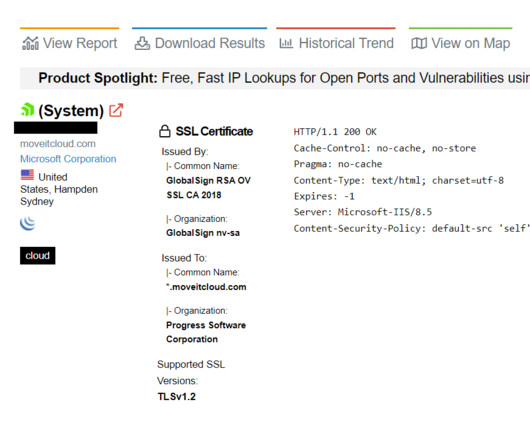
UK Payroll Provider Zellis' MOVEit Hack Affects British Airways, Boots and the BBC Microsoft says an affiliate of the Russian-speaking Clop ransomware gang is behind a rash of attacks exploiting a recently patched vulnerability in Progress Software's MOVEit application. Known victims include British payroll provider Zellis, which says eight corporate customers were affected.






































Let's personalize your content