Applying Data Retention Policies to Slack Data
Hanzo Learning Center
OCTOBER 19, 2021
Be honest: does your office look like this?

Hanzo Learning Center
OCTOBER 19, 2021
Be honest: does your office look like this?

Data Breach Today
OCTOBER 19, 2021
Officials: Threats to Sector Rising In Wake of Recent Hospital Ransomware Attack Israeli officials say they have fended off a wave of attempted cyberattacks on several hospitals and healthcare entities in recent days, as Hillel Yaffe Medical Center continues to recover from a ransomware attack last week that authorities reportedly suspect was carried out by Chinese hackers.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
OCTOBER 19, 2021
Most of the people I know professionally and personally don’t spend a lot of time contemplating the true price we pay for the amazing digital services we’ve all become addicted to. Related: Blockchain’s role in the next industrial revolution. I’ll use myself as a prime example. My professional and social life revolve around free and inexpensive information feeds and digital tools supplied by Google, Microsoft, Amazon, LinkedIn, Facebook and Twitter.
Data Breach Today
OCTOBER 19, 2021
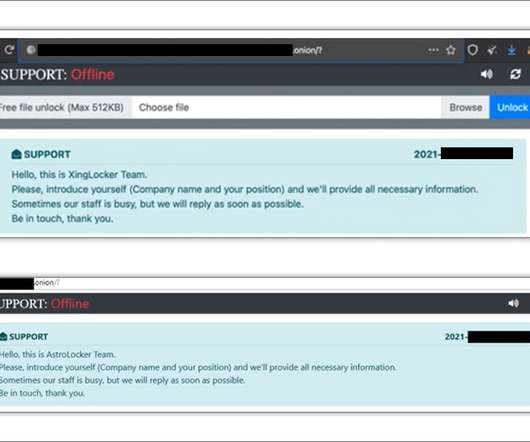
Trend Micro: Operators Rebrand "Supplier" Ransomware Before Deployment Researchers at cybersecurity firm Trend Micro have observed the adoption of a new franchise-based business model by ransomware operators that moves away from the traditional ransomware-as-a-service model. Operators now rebrand a "supplier" ransomware before deployment.

Advertisement
Generative AI is upending the way product developers & end-users alike are interacting with data. Despite the potential of AI, many are left with questions about the future of product development: How will AI impact my business and contribute to its success? What can product managers and developers expect in the future with the widespread adoption of AI?

Schneier on Security
OCTOBER 19, 2021
Researchers trained a machine-learning system on videos of people typing their PINs into ATMs: By using three tries, which is typically the maximum allowed number of attempts before the card is withheld, the researchers reconstructed the correct sequence for 5-digit PINs 30% of the time, and reached 41% for 4-digit PINs. This works even if the person is covering the pad with their hands.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Security Affairs
OCTOBER 19, 2021
FBI, CISA, NSA have published a joint advisory about the operation of the BlackMatter ransomware gang and provides defense recommendations. The Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the National Security Agency (NSA) have published an advisory that provides details about the BlackMatter ransomware operations and defense recommendations.

Data Breach Today
OCTOBER 19, 2021
Tells 3 Others to Provide Information in Latest Crypto Enforcement Effort New York State AG Letitia James served cease and desist letters to two cryptocurrency lending platforms that her office says engage in "unregistered and unlawful activities." Three other platforms were told by the OAG to "immediately provide information about their activities and products.

Data Matters
OCTOBER 19, 2021
The U.S. Federal Trade Commission (FTC) on October 13 published a Notice of Penalty Offenses advising more than 700 companies that they could incur significant civil penalties if they use endorsements in ways that run counter to the FTC’s guidance. The FTC, in its own words, “blanket[ed] industry” with these notices to send a “clear message” that companies cannot use “fake reviews and other forms of deceptive endorsements” to “cheat consumers and undercut honest businesses.”.

Threatpost
OCTOBER 19, 2021
The out-of-bounds read vulnerability enables an attacker to escape a Squirrel VM in games with millions of monthly players – such as Counter-Strike: Global Offensive and Portal 2 – and in cloud services such as Twilio Electric Imp.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Jamf
OCTOBER 19, 2021
Jamf’s own Protect Detections Team presents a State of the Union of macOS malware, including which ones are the greatest concern, how they they infect endpoints and what they do once they’re installed. They also go over malware protection for Mac.

Threatpost
OCTOBER 19, 2021
An advisory by the CISA, FBI and NSA reveals hallmark tactics of and shares defense tips against the cybercriminal group that’s picked up where its predecessor DarkSide left off.
Security Affairs
OCTOBER 19, 2021
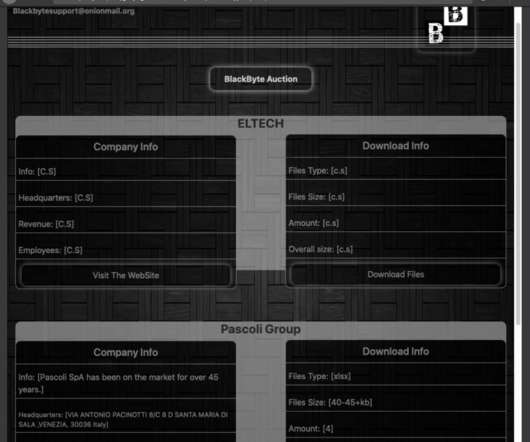
Trustwave’s SpiderLabs researchers have released a free decryptor for the BlackByte ransomware that can allow victims to recover their files. Researchers from Trustwave’s SpiderLabs have released a decryptor that can allow victims of the BlackByte ransomware to restore their files for free. The experts spotted the BlackByte ransomware while investigating a recent malware incident.

Rocket Software
OCTOBER 19, 2021
For Rocket to succeed and better serve customers, we need to invest in our greatest asset – our employees. This means encouraging every Rocketeer to show up as their whole self and amplifying diverse voices across the organization to reflect our core values of empathy, humanity, trust and love. That’s why we’re so proud of our most recent Aurora graduates, a program by reacHIRE that partners with the Rocket Inclusion, Diversity and Equity (RIDE) initiative.

Advertisement
Start-ups & SMBs launching products quickly must bundle dashboards, reports, & self-service analytics into apps. Customers expect rapid value from your product (time-to-value), data security, and access to advanced capabilities. Traditional Business Intelligence (BI) tools can provide valuable data analysis capabilities, but they have a barrier to entry that can stop small and midsize businesses from capitalizing on them.

Dark Reading
OCTOBER 19, 2021
Why understanding human behavior is essential to building resilient security systems.
Thales Cloud Protection & Licensing
OCTOBER 19, 2021
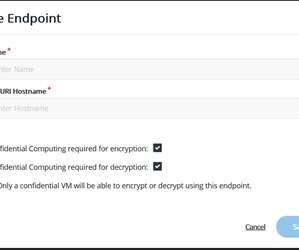
CipherTrust Data Security Platform now allows users to control encryption keys for data processed by Google Cloud’s Confidential Computing. divya. Tue, 10/19/2021 - 06:19. The Thales partnership with Google Cloud takes a huge step forward with the announcement of Google Cloud ubiquitous data encryption. I’d like to review a few things before discussing the latest technology because this innovation builds on previous ones like a well-crafted skyscraper depends on a great foundation!

Threatpost
OCTOBER 19, 2021
Cybersecurity budget cuts are everywhere. Chad Anderson, senior security researcher at DomainTools, discusses alternatives to fancy tooling, and good human skills alignment.

Dark Reading
OCTOBER 19, 2021
Analysis of the top-50 multiparty attacks over the past decade finds that nation-state-linked hackers focused on disruption and using stolen credentials cause the most damage.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

DXC Technology
OCTOBER 19, 2021
??????????????????????????????????????????????????????????????????????????????????????????? ?????????????????????????????????????????????????????????????????????????????????????????????UI??????????????????UX?????? ?????????????????????????????????????????UI????UX?????????????????????????????????????????????????????????? PC??????????????????Web????????????
Security Affairs
OCTOBER 19, 2021
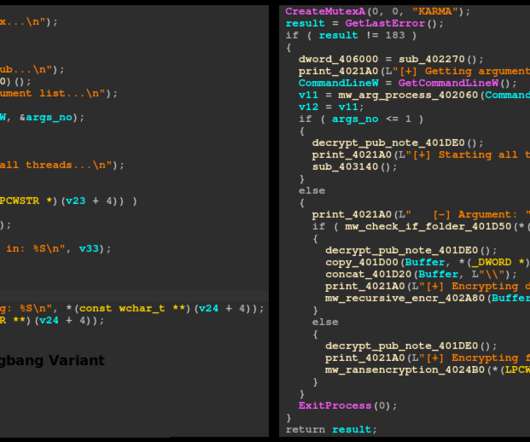
Sentinel Labs experts have analyzed the new Karma ransomware and speculate it represents an evolution of the Nemty ransomware operation. Karma ransomware is a new threat that was first spotted in June of 2021, it is important to distinguish it from a different threat with the same name that is active since 2016. Sentinel Labs researchers explored the links between the Karma ransomware and other malware families such as NEMTY and JSWorm.

Jamf
OCTOBER 19, 2021
IT admins often ask questions about best practices when using Jamf Pro for Apple device management. Two Jamf engineers, Bryson Tyrrell and Dr. Emily Kausalik-Whittle, use this JNUC session to sketch a framework for approaching best practices in the software.

Dark Reading
OCTOBER 19, 2021
Ferrara Candy Co. said a ransomware attack earlier this month won't affect Halloween supplies of its sweets, which include Brachs, Keebler, Sweet Tarts, and other popular brands.

Advertisement
While data platforms, artificial intelligence (AI), machine learning (ML), and programming platforms have evolved to leverage big data and streaming data, the front-end user experience has not kept up. Holding onto old BI technology while everything else moves forward is holding back organizations. Traditional Business Intelligence (BI) aren’t built for modern data platforms and don’t work on modern architectures.

Threatpost
OCTOBER 19, 2021
TA505 – cybercrime trailblazers with ever-evolving TTPs – have returned to mass-volume email attacks, flashing retooled malware and exotic scripting languages.

Schneier on Security
OCTOBER 19, 2021
According to a report from CISA last week, there were three ransomware attacks against water treatment plants last year. WWS Sector cyber intrusions from 2019 to early 2021 include: In August 2021, malicious cyber actors used Ghost variant ransomware against a California-based WWS facility. The ransomware variant had been in the system for about a month and was discovered when three supervisory control and data acquisition (SCADA) servers displayed a ransomware message.

Dark Reading
OCTOBER 19, 2021
Attackers use a different set of techniques to target the cloud, meaning defenders must think differently when pen testing cloud environments.

Threatpost
OCTOBER 19, 2021
The APT, which targets Middle-Eastern energy firms & telecoms, has been relatively quiet since its exposure but not entirely silent. It's kept up attacks through 2021 and is working on retooling its arsenal yet again. .

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Thales Cloud Protection & Licensing
OCTOBER 19, 2021
Licenses vs. Entitlements: Know your rights. riddhi. Tue, 10/19/2021 - 08:16. Updated. How can you ensure that your company is complying with its contractual obligations around the use of third-party software? Moreover, how can you be sure that those software assets are being properly utilized? It all starts by understanding the fundamental difference between the terms ‘software license’ (or licensing) and ‘entitlement’ (or entitlement management).

Dark Reading
OCTOBER 19, 2021
Data in Dark Reading's 2021 Strategic Security Survey report suggest organizations are taking the security challenge seriously.

Threatpost
OCTOBER 19, 2021
The group is likely nation-state-backed and is mounting an ongoing spy campaign using custom malware and stealthy tactics.
Let's personalize your content