REvil Ransomware Gang Threatens Stolen Apple Blueprint Leak
Data Breach Today
APRIL 21, 2021
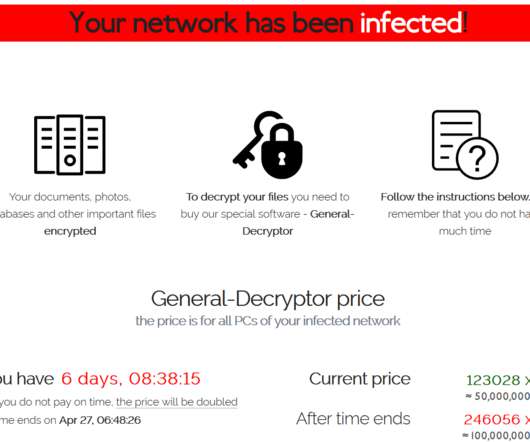
$50 Million Extortion Demand Issued to Apple and Taiwanese Manufacturer Quanta The REvil - aka Sodinokibi - ransomware gang is threatening to release stolen Apple device blueprints unless it receives a massive payoff. The extortion threat - with a reported $50 million opening demand - was unveiled hours before Apple made a series of major new product announcements.








































Let's personalize your content