9 Cybersecurity Takeaways as COVID-19 Outbreak Grows
Data Breach Today
MARCH 18, 2020
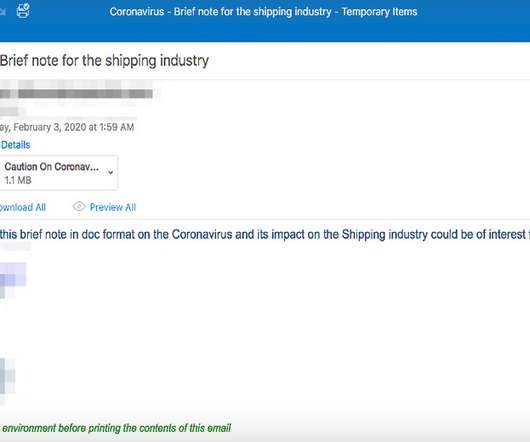
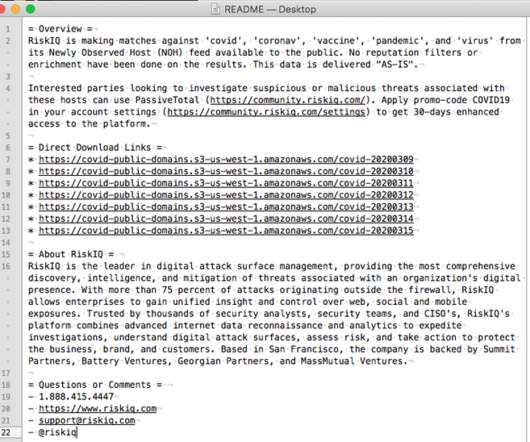
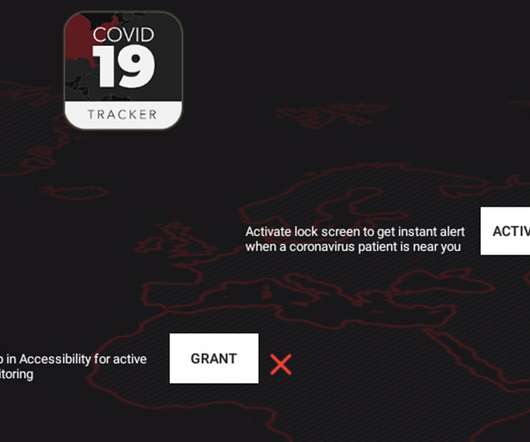
Attackers Already Targeting Remote Workers With Phishing Campaigns As a result of the COVID-19 outbreak, cybercriminals increasingly are targeting organizations that now have more remote workers and fewer IT and security staff at the ready to mitigate hacker attacks and intrusions, security experts say.






































Let's personalize your content