Enel Group suffered the second ransomware attack this year
Security Affairs
OCTOBER 27, 2020
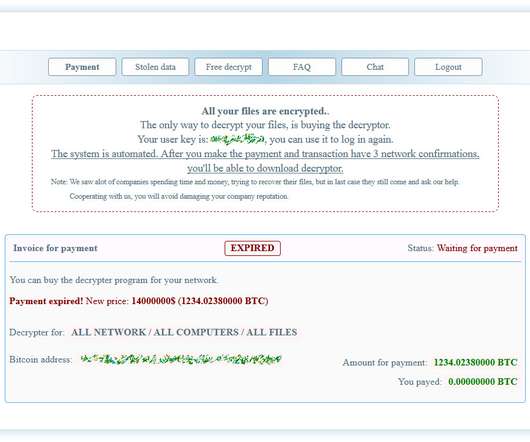
The Italian cyber security firm TG soft publicly shared the news of the attack in a tweet: 2020-10-27 #Enel colpita di nuovo da #ransomware. The hackers stole about 5 terabytes of documents from the company and announced that they will “analyze every file for interesting things” and publish it on their leak site.














Let's personalize your content