China-linked APT Sharp Panda targets government entities in Southeast Asia
Security Affairs
MARCH 8, 2023
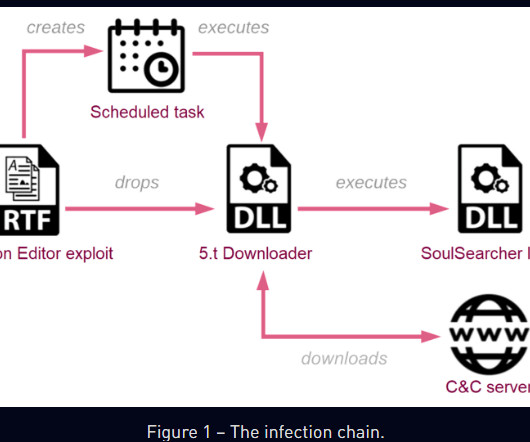
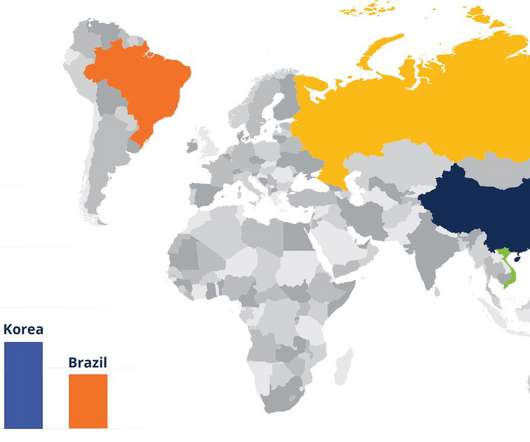
China-linked APT group Sharp Panda targets high-profile government entities in Southeast Asia with the Soul modular framework. CheckPoint researchers observed in late 2022, a campaign attributed to the China-linked APT group Sharp Panda that is targeting a high-profile government entity in the Southeast Asia.














Let's personalize your content