More details about Operation Cronos that disrupted Lockbit operation
Security Affairs
FEBRUARY 20, 2024
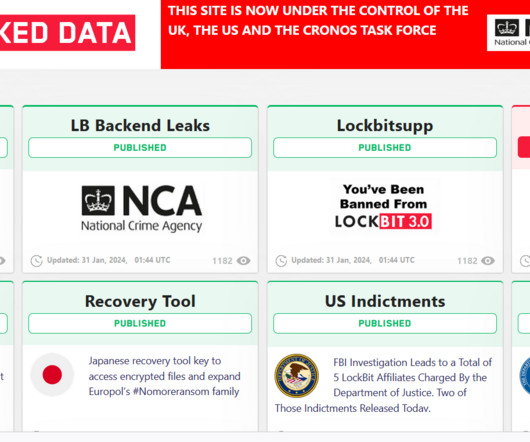
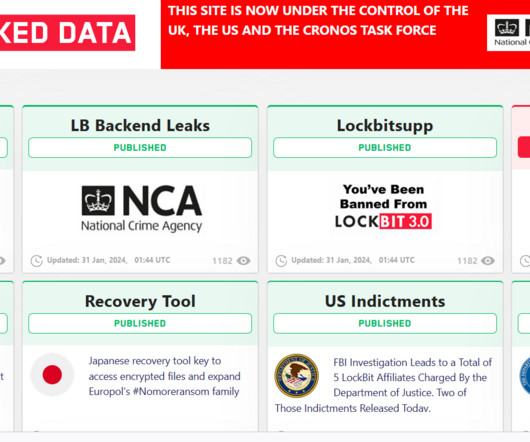
Yesterday, a joint law enforcement action, code-named Operation Cronos , conducted by law enforcement agencies from 11 countries disrupted the LockBit ransomware operation. “LockBit had a bespoke data exfiltration tool, known as Stealbit, which was used by affiliates to steal victim data.















Let's personalize your content