Hackers are again attacking Portuguese banking organizations via Android Trojan-Banker
Security Affairs
APRIL 16, 2020
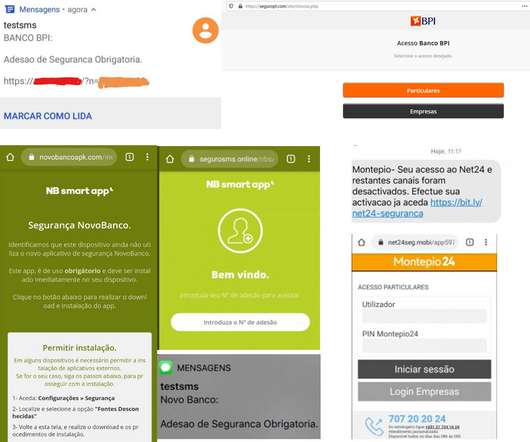
The threat is not new, hackers are again attacking clients of Portuguese banking organizations via a specially crafted Android Trojan-Banker from phishing campaigns launched from Brazil. Figure 1: 0xSI_f33d – feed that compiles phishing and malware campaigns targeting only Portuguese citizens. The token is sent to the backoffice.












Let's personalize your content